 |
Interesting Articles about Popular Topics |
|
|
Dave Carlson - June 2, 2014 AbstractBiometrics is a specific process of gathering and examining distinctive identifiers and measurable characteristics to identify individuals. Security often is achieved by verifying something you know (e.g. password), something you have (e.g. smartcard), or something you are (e.g. fingerprint). Biometric features are the most accurate method of human identification, since only biometrics can verify that you are you. There are two biometric modalities: physiological (distinctive attributes of the human body) and behavioral (distinctive behavioral patterns of a person). This article limits the scope of discussion to three popular biometric physiological characteristics used to grant access to automation systems and facilities: fingerprints, iris scan, and facial recognition. IntroductionBiometrics is a specific process of gathering and examining distinctive identifiers and measurable characteristics to identify individuals. Biometric features are the most accurate method of human identification. Fingerprints and DNA analysis have been used for many years. Facial recognition and retina scans are accepted procedures to verify a person’s uniqueness. Documents, such as identification cards, can easily be altered and can be difficult to interpret if they are in a language unfamiliar to the reader. However, fingerprints and other biometric features cannot be altered without extensive effort and are universally accepted as a verification of identity. Security often is achieved by verifying something you know (e.g. password), something you have (e.g. smartcard), or something you are (e.g. fingerprint). The U.S. Department of Defense (DoD) teaches in their Biometrics Awareness Course that only biometrics can verify that you are you. Identification cards or access tokens (smartcards, etc.) are not a part of you and can be lost, stolen, or (sometimes) duplicated. Passwords and pass phrases are not a part of you and can be forgotten, shared, observed, or broken. Only you can verify that you are you with the highest degree of accuracy. Biometric ModalitiesThere are two types of biometrics (called modalities) -- physiological and behavioral.
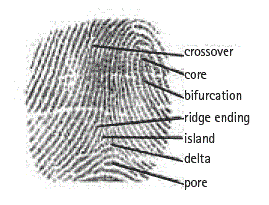
This article will limit the scope of discussion to three popular biometric physiological characteristics used to grant access to automation systems and facilities: fingerprints, iris scan, and facial recognition. Fingerprints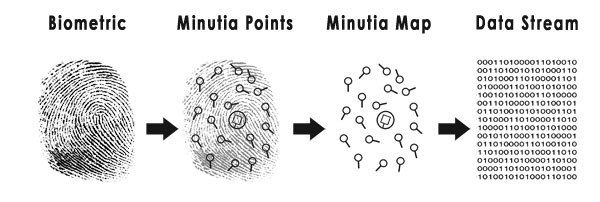 Among all the possible biometric signs, forensic and security personnel have observed fingerprints the longest. No two fingerprints are alike (even belonging to the same person). Fingerprint characteristics are features on the friction ridges of the skin. These ridges begin to form while inside the womb and grow proportionally as the baby grows. The ridges remain the same throughout a person's life and for a time after death. Damage to the skin which penetrates through the outer skin layer (epidermis) to the inner layer (dermis) will cause scarring and permanently alter ridge alignment. Friction ridges form patterns in distinct main types (whorl, loop or arch) which allows for classification. The ridges are not continuous lines but may for example:
 There are three types of fingerprints: latent, patent, and plastic.
The person credited with developing the first fingerprint identification system is Sir Edward Henry. In 1900 Sir Henry published his book Classification and Uses of Fingerprints. In his book, he revealed his classification system depicting Right Loop (R), Left Loop (L), Whorl (W), Arch (A), and Tented Arch (T). By 1910, Sir Henry's classification system was the basis of identification by police forces and prison authorities throughout the English-speaking world. 




While recovering fingerprint evidence is helpful for criminal investigations, fingerprints used for security purposes are captured directly from a person’s finger. Most common are index finger and thumb recognition. A security device captures a person’s fingerprints when the person wishing to be identified presses their finger on the scanning window. 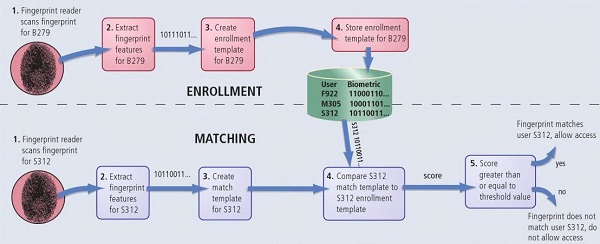
Two Steps in Biometric Fingerprint Technology Occasionally distortions of a fingerprint (e.g. grease, dirt, and paint) make it a challenge to achieve positive identification when compared to a reference sample. Because of this challenge, scientists have developed complex computational algorithms to create highly accurate comparisons between fingerprint samples. These algorithms have allowed fingerprint identification to move from the realm of professional opinion to defined universal science. The science allows for commercial adaptation, such as integrating fingerprint scanners on notebook computers. Many portable computer systems now offer fingerprint biometric protection from unauthorized access. Iris Scan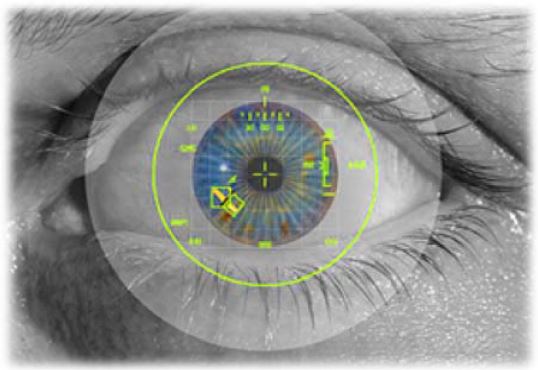 Iris scanning is very accurate. The iris is a visible (yet protected) structure that usually does not change over time, making it ideal for biometric identification. Eyeglasses and contact lenses typically do not interfere with image capture or cause inaccurate readings. Blind people can use iris scanners as long as their eyes have irises. Even eye surgery does not change identifying iris properties for most people (with the exception of some types of cataract surgery). Sophisticated modern iris scanning systems, like those used by the United States Department of Defense, compare 950 different characteristics to uniquely identify a person’s iris. This huge amount of unique data points can provide an accuracy level of only one false match in 1.2 million scans. Some forensics experts claim that the chance of two individuals having the same iris pattern is 1 in 10 to the 78th power. Because some modern iris scanners can handle around 2,000 data points (compared to about 100 for a fingerprint) an iris scan rarely results a false positive. The human iris begins to form during the third month of gestation. Structures creating its distinctive pattern are complete by the eight month of gestation. However, iris pigmentation continues to develop and change for several years after birth. The layers of the iris have both ectodermal (outer layer) and mesodermal (middle layer) embryological origin, consisting of (from back to front):
Iridian Technology suggested some advantages of using iris recognition:
An iris scanning system employs a CCD digital camera sensor using both visible and near-infrared light to capture a clear, high-contrast image of a person's iris. The computer connected to the camera identifies center of the pupil, edge of the pupil, edge of the iris, eyelids, eyelashes, and all related data. After locating the eye structures and collecting all the data points, the computer software analyzes patterns in the iris and generates a unique code and stores it in a database for future retrieval and recognition. By translating the image into a digital code, the system can store and compare much more data than if it had to analyze a complete image each time it needed to verify someone. Facial Recognition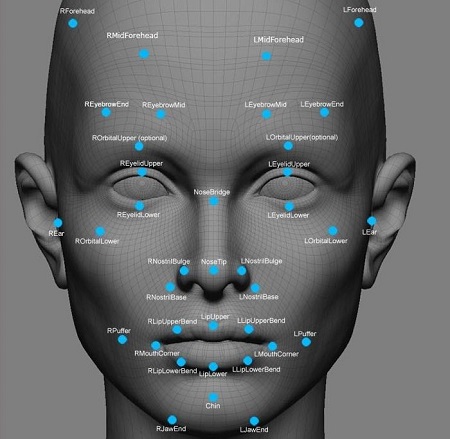

Facial Recognition Algorithm Representation and a Facial Scanning System The science of facial recognition involves the study of how people recognize faces and determining ways to emulate this process with computer systems. Just like humans use their eyes to gather information to determine facial recognition, computer systems use visual sensors to capture images. Humans use their brains to process facial recognition, while computer systems use hardware and software to replicate the process. Some computer sensors are video camera, CCD cameras, infrared cameras, and 3D scanning systems. One of the challenges to accurate facial recognition is facial detection. Not only does a reliable facial recognition system need to identify a face, but it first needs to find the face. The system needs procedures to detect specific facial components and orient these components relative to each other. It then uses an algorithm to convert this data to a form a computer can use to locate a representative sample. This process is made more difficult by face positioning (e.g. head tilted left of right), face distance (e.g. head tilted forward or backward), face obscuration (e.g. hair in different positions), and a multitude of additional physical factors. FST21, a New York City company, offers a building security system that eliminates the need for keys by combining facial recognition with other biometric sensors. The system uses sophisticated scanners to recognize a person’s face, voice, build, and stride. Once the system identifies the appropriate person it can unlock their door in less than two seconds. Any strangers not in the database will be denied access. "This is only the beginning," says General Aharon Farkash, the founder and president of the firm FST21. "This is the way people will enter buildings in the 21st century." The main facial recognition methods are: feature analysis, neural network, eigenfaces, automatic face processing, and three-dimensional facial recognition. Bruce and Young developed the best-known face recognition model in 1986. They based their study on an established four-step human cognitive process for recognizing a known face:
Facial recognition systems can be effective in security situations. The systems are most effective if the target image is well-documented in the facial recognition system. Under controlled conditions (e.g. office environment) these systems can be extremely accurate. A good use for these systems is to allow computer user access. The user looks into a camera so the facial recognition system can identify the person and allow access to the computer. Summary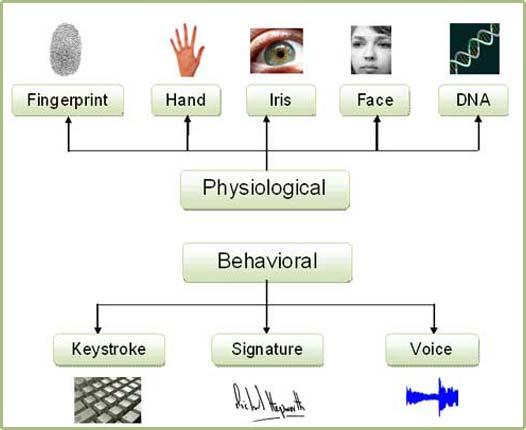 Biometrics is a process of gathering and examining distinctive identifiers and measurable characteristics to identify individuals. Biometric features are the most accurate method of human identification, since only biometrics can verify that you are you. There are two biometric modalities: physiological (distinctive attributes of the human body) and behavioral (distinctive behavioral patterns of a person). This paper discussed three popular biometric physiological characteristics used to grant access to automation systems and facilities: fingerprints, iris scan, and facial recognition. REFERENCES - BIOMETRICSFor further study, you may find the following list of biometrics references helpful. The author reviewed these references during the development of this article.
|
||||
|
