 |
Interesting Articles about Popular Topics |
|
|
Dave Carlson - March 7, 2013 Workers are using electronic devices at work and connecting them to company networks. The industry has identified this phenomenon as Bring Your Own Device (BYOD). IT managers need to prepare for this security issue, because it is not going away. "BYOD allows collaboration, sharing of resources, and mirrors the outside world." (Stager, p. 5) A study by CDW estimates that up to 94% of employees have used BYOD to increase their work efficiency (Carlson, p. 1). The two main types of personal gadgets workers are bringing to work are smartphones and tablets (see Figure 1). 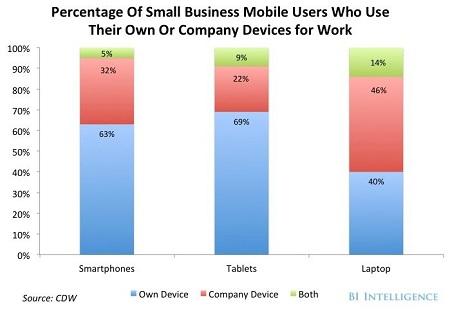
Figure 1. Mobile Devices Used for Work (Carlson, 2013, ¶ 1) An upside to allowing BYOD on your company network may be increased productivity it offers workers. However, there also is a risk that by encouraging staff to bring in their own devices that are more suited to watching videos, playing games, and keeping their digital social lives current, they will do just that. (Ranger, ¶ 9) A significant down side of allowing BYOD on your network may be increased aggravation and costs. You need to evaluate both the pros and cons before you decide if BYOD is right for your organization. Drain on Network Authentication ResourcesBYOD can put a significant burden on an organization's wireless network. Because many workers are using personal devices at work, IT departments have no effective visibility or control on the number and type of devices accessing the network. Without effective access control, a wireless device will connect to whatever network SSID that is accessible. Generally, this is whatever network point is listed in the device as the last connection. As people move around the organization, their device may hop to another network point without releasing the connection resource of the original connection. Even if the device does not connect to the network it can drain network resources trying to authenticate all of the various BYOD requests. Consumption of Available Network BandwidthIn addition to taxing network authentication resources, BYOD access by an unrestricted number of wireless devices also can suck up all available free bandwidth. This is especially a problem when people roam around the organization, since if the device is turned on, it will try to connect. The same way BYOD controls network access resources, it can consume bandwidth that may be better used by something else. Many times, IT department has no visibility on these resource-draining electronic vampires. Additional Demand on Help Desk StaffA decrease of available resources (either hardware or bandwidth) will cause incremental problems with company devices for which the network originally was designed. The Help Desk will begin receiving more and more calls from irate users related to inability to connect to the network. Without an effective BYOD plan in place, IT managers will be hard pressed to determine why Help Desk calls are spiraling out of control. Increased personnel, expanded training, additional equipment, and more office space all can be by-products of an out-of-control BYOD culture. Increased Security ThreatsSecurity is a big issue with BYOD, because allowing personal consumer devices onto corporate networks can bring significant risks that need to be managed correctly (Ranger, ¶ 5). Allowing uncontrolled BYOD access to your network invites a plethora of security and compliance issues, “because you won’t know if devices contain malware or what they are doing on your network. And without effective network access control, you won’t be able to do anything about it" (Andrus, ¶ 7). Both security concerns for the organization and government compliance issues should be high on the list of company security managers. This is especially true for any firm that does business with the Federal Government. Overall Increase in Networking BudgetAs the drain on network hardware resources and bandwidth increases, so does the requirement for additional resources and bandwidth capacity. "Almost three quarters (73 per cent) of the 100 IT directors surveyed for research by IT services provider Damovo UK worry that BYOD will cause IT costs to 'spiral out of control'." (Heath, ¶ 2) Above additional costs, “the complexity of configuring access privileges for the plethora of devices under BYOD will place additional burden on the IT department.” (Heath, ¶ 6) In addition to the resources consumed by the BYOD device itself, many apps running on those devices demand an insatiable amount of network capability. Evaluate your evolving company culture to determine if BYOD is a concern for your organization. If it appears that personnel in the organization are pushing for and using BYOD, then IT professionals and organization management need to take appropriate action to mitigate the risks introduced by BYOD. To be successful, treat your users as adults, trust them to make the right decisions, and allow them to become a part of the solution instead of contributing to the problem. Understand the ProblemDetermine if your workers are part of the 94% illustrated in Figure 1. If they are, be aware of what devices they are bringing to work and how they are using them. Monitor your network activity to see if BYOD is making a significant impact (if so, it most likely is negative). Explore the possibility of legal impacts. If your organization is a government contractor, you may be open to more risks than if all your clients are in the private sector. The blending of personal and work lives on a single device open up a host of problems. “CIOs often fret about security and management, but BYOD can land a company in murky legal water, too.” (Kaneshige, ¶ 4) Establish a PolicyAn organization that allows BYOD access to their systems probably needs a policy to establish guidelines and procedures for BYOD. The policy could establish a mobile device management process that will establish centralized access privileges. Additionally, the organization could “set up corporate stores of centrally sanctioned apps that users can access with their device.” (Heath, ¶ 7) In any event, it may be a resource and budget issue. A strict BYOD policy may need to be in place and enforced to minimize increased costs of BYOD interaction with company systems. (Marks, ¶ 7) While it is important to establish a policy to protect the organization’s network assets, the policy should be flexible enough to allow workers to do their job. Ensure the policy finds a good balance between security that restricts any meaningful access and an open environment that invites risks. Policies that assume users are adults, explain reasons for the rules, and provide appropriate software, generally are “more successful than multi-layer approvals and draconian prohibitions.” (Gray, ¶ 3) The person responsible for writing the BYOD policy needs to include all stakeholders in the design of the policy. This is critical to establish buy-in and support for the policy. The first person to get on board is the most highly-placed decision maker in the organization. As with any company-wide project, the BYOD policy writer should get a charter from the decision maker which gives her the authority and guidance necessary to draft an effective policy. Enforce the PolicyPolicies and rules have no effective meaning if they are not enforced. The policy should include a section that clearly specifies the penalties for non-compliance. The managers and supervisors responsible for enforcing the BYOD policy need to be consistent in their actions. If something is not enforced because it does not make sense, then the policy should be changed to reflect the appropriate guidance. Workers should be required to read the policy and sign an agreement to follow the policy. Of course, you need to get your legal department involved to ensure you do it the right way. The bottom line is that it is easier to get people to support policies if they know they will be held accountable. If you are going to have a policy, then you need to ensure that policy is enforced consistently throughout the organization. Many users intuitively understand the need to protect proprietary data, and will comply with policies that protect the data. Make it easy for users to protect data via software and configuration checklists. Use IT tools that identify missed settings or installations related to protecting data. If you assume that users will protect corporate data, given proper tools and job aids, you will be more likely to design a program that makes for easier compliance. Conversely, if you assume you must apply an antiquated managed device paradigm to BYOD, you most likely will end up treating users as risks rather than partners in protecting data. Find a balance that is right for your organization and your users will help you maintain BYOD security. (Gray, ¶ 6) BYOD encroachment on the corporate landscape appears to be unavoidable. In fact, for many firms, it is already here. It certainly appears to be a future part of world-wide business culture. Managers need to be aware of the issue, understand the problems for their organization, establish an effective BYOD policy, and put measures in place to enforce the rules. Of course, the policy and culture needs to remain flexible enough to create a BYOD policy that will meet the needs of the organization. Andrus, F. (2013, March 6). The hidden problems of BYOD: What you don't know will cost you. Bradford Networks. Retrieved March 6, 2013 from http://www.bradfordnetworks.com/the-hidden-problems-of-byod-what-you-dont-know-will-cost-you Carlson, N. (2013, January 8). Which Gadgets Are Employees Bringing To Work That IT Managers Need To Worry About? Business Insider. Retrieved March 6, 2013 from http://www.businessinsider.com/employee-gadgets-it-managers-should-worry-about-2013-1 Gray, P. (2013, February 18). Three BYOD policies for keeping workers (and IT) happy. TechRepublic. Retrieved March 7, 2013 from http://www.techrepublic.com/blog/tech-manager/three-byod-policies-for-keeping-workers-and-it-happy/8142 Heath, N. (2012, June 27). BYOD will push up IT costs, say tech chiefs. CIO Insights. Retrieved March 6, 2013 from http://www.techrepublic.com/blog/cio-insights/byod-will-push-up-it-costs-say-tech-chiefs/39748942 Kaneshige, T. (2012, May 9). BYOD Stirs Up Legal Problems. CIO. Retrieved March 6, 2013 from http://www.cio.com/article/706086/BYOD_Stirs_Up_Legal_Problems Marks, G. (2013, February 25). Do you really need a BYOD policy? Forbes. Retrieved March 7, 2013 from http://www.forbes.com/sites/quickerbettertech/2013/02/25/do-we-really-need-a-byod-policy/ Ranger, S. (2012, July 5). BYOD: 10 reasons it won't work for your business. ZD Net. Retrieved March 6, 2013 from http://www.zdnet.com/byod-10-reasons-it-wont-work-for-your-business-7000000050/ Stager, G. S. (2012, February). Is BYOD the answer to our problems or the worst idea ever? Learning & Leading with Technology, pp. 5-8. |
||||
|