 |
Interesting Articles about Popular Topics |
|
|
Dave Carlson - November 13, 2007 Both physical and digital crime scene investigations are composed of basic building blocks: preserve the scene; survey for evidence; document evidence and scene; search for evidence; reconstruct the scene; and present a theory. Physical and digital evidence together create a complete theory about the crime scene. A digital investigator should assume that key digital evidence may be protected by encryption or code. Yet, the investigator must not overlook the obvious—sometimes criminals make no extra effort to cover their tracks. The most important aspect of digital evidence is to preserve the original state of the data. Always investigate on a copy. Ultimately, the forensic investigator must create the entire who, what, when, where, why, and how of the incident. There is no single way to conduct an investigation. If you ask five people to find the person who drank the last cup of coffee without starting a new pot, you will probably see five different approaches. One person may dust the pot for fingerprints, another may ask for security camera tapes of the break room, and another may look for the person with the hottest cup of coffee. As long as we find the right person and do not break any laws in the process, it does not matter which process is used, although some are more efficient than others (Carrier, 2005, p. 5). Carrier and Spafford (2003) taught that all crime scene investigations were composed of basic building blocks (p. 8). Digital investigations enhance standard physical crime scene investigations, rather than replace anything from crime scene investigation’s best practices. Figure 1 demonstrates how physical and digital crime scene investigations complement each other. Physical and digital evidence together create a complete theory about the crime scene. 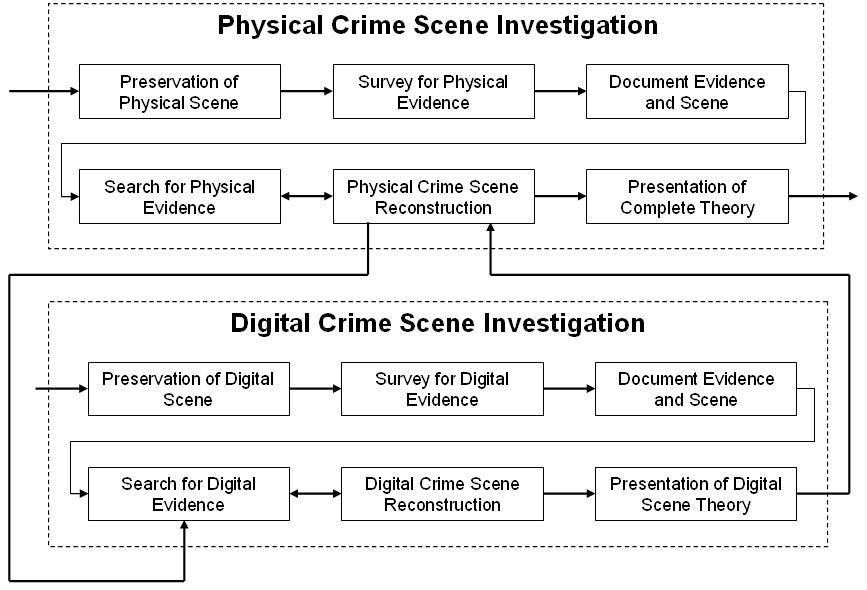
Figure 1. Physical and digital crime scene investigation interaction (derived from Carrier & Spafford, 2003, pp. 8-10). The focus of this paper will be on the Digital Crime Scene Investigation aspect of crime scene investigation interaction. The first part of this paper will discuss unique problems that face computer investigators. The second part of this paper will discuss concerns related to encryption, code, and compression as they relate to increasing the difficulty of investigations for digital detectives. The FBI and other law enforcement agencies started to look at ways to examine computer evidence as early as 1984 (Whitcomb, 2002, p. 1). The international community tried to formalize the examination of computer evidence during the International Hi-Tech Crime and Forensics Conference held in London in October 1999. Three years later, Whitcomb (2002) attempted to describe the intent of examining computer evidence: “to ensure that digital evidence is collected, preserved, examined, or transferred in a manner safeguarding the accuracy and reliability of the evidence, law enforcement and forensic organizations must establish and maintain an effective quality system” (p. 4). Michael Bacon, a computer forensics advocate from the United Kingdom, maintained that “the police find it easier to prosecute speeders than electronic crime – cynical, but true” (Armstrong, 2002, p. 7). Part of the difficulty in prosecuting digital criminals in the past was the form and availability of evidence gathered against them. It is the forensic investigator’s job to conduct a professional and supportable investigation to find the appropriate digital evidence. Even though “currently there is no established standard method for conducting a computer forensic examination” (Carney & Rogers, 2004, p. 2), best practice for computer investigations has evolved to dictate that a digital crime scene investigator follows the same proven techniques employed by physical crime scene investigators (Carrier & Spafford, 2003, p. 8). Even though the basic process of investigation is the same in the physical and digital world, the approach and methods are unique in an investigative world where representations of ones and zeros frequently are more important evidence than what can be touched and tagged. Preservation of Digital SceneThis discussion of preservation of the digital scene assumes that the physical scene has been preserved. The investigator must choose the method for preserving the original digital crime scene, based on all known factors surrounding the situation. “Deciding whether to let a machine continue to run, to pull the power plug from the back of the computer, or to perform the normal administrative shutdown process is one of the longest running arguments in the computer forensics field” (Kruse & Heiser, 2002, p. 5). It is beyond the scope of this paper to discuss detailed pros and cons for each course of action. Whatever decision the investigator makes about the course of action chosen to preserve the digital crime scene must be clearly explained and well documented. “Documentation is paramount to any investigation and should not be overlooked” (Jones, Bejtlich, & Ruse, 2006, p. 166). The ultimate outcome is to be able to prove that the digital evidence has not been altered from its original state upon discovery. It is difficult to prove that any kind of collected evidence, especially digital evidence, is the same as what the suspect originally left behind (Kruse & Heiser, 2002, p. 13). Anything an investigator does to a system will make some change to the state of the system since the suspect last touched the evidence. The Locard Exchange Principle is a theory accepted in many physical crime scene investigations. The theory states, “when two objects come into contact, a mutual exchange of matter will take place between them” (Carrier and Spafford, 2003, p. 5). The goal for preserving the scene is to do everything reasonable to reduce the amount of data that is changed (Carrier, 2005, p. 6). Brown (2006) shared “the golden rule of evidence dynamics: be as least intrusive as possible” (p. 44). A digital investigator’s ultimate objective is to “safeguard the original evidence” (Kruse & Heiser, 2002, p. 325). Kruse and Heiser (2002) recommended making two backups of the original data (p. 14). This allows the investigator to preserve the original evidence in the same condition it was discovered and allowing the investigation to start “at the beginning” whenever necessary. Having a second backup also will demonstrate extra care to preserve the original evidence. Survey for Digital EvidenceFollowing the digital investigator’s prime directive to “safeguard the original evidence,” the investigator should, whenever possible, survey the digital evidence on a copy of the original data. Kruse and Heiser (2002) recommended following these steps when surveying for digital evidence:
Jones, Bejtlich, and Rose (2006) recommended that the first step in surveying for digital evidence should be to recover any deleted files and add them to the analysis (p. 207). Experienced investigators have discovered that suspects frequently delete most of the information that is relevant to an investigation (p. 207). It is beyond the scope of this paper to discuss details of how to recover deleted files, but there are a number of commercial and open source tools available to the forensic investigator. Document Evidence and Scene“Documentation is paramount to any investigation and should not be overlooked” (Jones, Bejtlich, & Rose, 2006, p. 166). Jones, Bejtlich, and Rose (2006) recommended the following types of documentation for a digital investigation: evidence worksheets, system worksheets, agent notes, evidence labels, chain of custody forms, evidence custodian logs, and evidence access logs (p. 167). The types of forms used are not as important as some method to document as much information as is reasonable concerning the evidence and the immediate scene. Keep in mind that the immediate scene may physically be thousands of miles away if the investigation involves networks and remote sites. Search for Digital EvidenceKruse and Heiser (2002) advocated the more-is-better theory of evidence collection. “The more evidence that’s gathered, the better chances of developing a reliable list of suspects” (p. 312). Frequently, it is imperative to collect appropriate evidence as quickly as possible, as some digital evidence is very volatile. “The longer the delay, the less likely that a suspect can be located” (Kruse & Heiser, 2002, p. 312). Rowlingson (2004) suggested the following basic questions to identify possible evidence sources for data:
Sometimes a search for evidence is obscured by digital encryption, code, or compression. This topic will be covered in more detail in the second section of this paper. Digital Crime Scene ReconstructionDigital crime scene reconstruction may be the most challenging part of the forensic investigator’s case. This author is not aware of a successful counter to the defense that a Trojan horse or virus installed on the computer may have been responsible for the presence of evidence. Carney and Rogers (2004) cited cases in England and the United States (Regina v. Greene and Regina v. Caffrey) that “have already proven the effectiveness of this defense” (p. 1). The statement made by Carney and Rogers (2004), “as yet, there is no reliable way to counter the Trojan defense” (p. 1) may be questioned by competent forensic examiners, but the fact remains that forensic examination is a developing field, subject to Dauber demands of documenting expert procedures (Carney & Rogers, 2004, p. 1). It is the forensic investigator’s job to use his or her best professional judgment about what actually happened at the time of the alleged incident. The investigator must demonstrate with words and recreations in a believable and legal manor the most likely course of events related to the alleged incident (Rowlingson, 2004, p. 22). Experience and professional judgment is paramount when attempting to reconstruct a historical incident with no living witnesses. Presentation of Digital Scene TheoryFollowing a credible recreation of the scene at the time of the incident, the investigator must “present an evidence-based case describing the incident and its impact” (Rowlingson, 2004, p. 22) through credible evidence and logical argument. It is time for the forensic investigator to create the entire who, what, when, where, why, and how of the incident. Rowlingson (2004) recommended that the presentation of digital scene theory include at least the following components:
Searching for digital evidence is similar to searching for physical evidence. An investigator’s grand prize frequently is the proverbial smoking gun. Unfortunately, if the investigator does not know the key evidence is locked in an unknown safe, it will be impossible to find the critical evidence. Kruse and Heiser (2002) claimed that a significantly challenge to a forensic investigator is the possibility of data being intentionally hidden by a suspect (p. 105). Even after an investigator discovers hidden data, the possibility of that data being relatively inaccessible exists. Encryption, code, and compression can be thought of as forms of digital safes. Before the digital investigator can find critical evidence, he must locate and unlock the digital safe securing that elusive evidence. “Finding a way to crack encryption has typically baffled law enforcement agencies” (Weimann, 2006, p. 187). A reasonable assumption for the digital investigator is to assume some key piece of digital evidence is protected by encryption or it is stored in a format other than plain text. However, the investigator must not overlook the obvious. Sometimes criminals make no effort to cover their tracks. Unfortunately, it is not reasonable to assume that recovery of data will be easy. Assuming the perpetrator was not careless enough to leave critical evidence in an open text file, the investigator must face cracking the digital safe. Three common methods employed to recover encrypted data are to locate the encryption key, conduct a software attack, or use keystroke capture methods (Weimann, 2006, p. 188). Locate Encryption KeyThe easiest way to access encrypted data “is to obtain the key, either by finding it or by asking someone who knows it” (Kruse & Heiser, 2002, p. 109). The investigator should anticipate finding encrypted data on a computer seized as evidence, so it should become instinctive to also look around for passwords. Some common locations for finding passwords are under the keyboard, around the desk, or in a Rolodex (Kruse & Heiser, 2002, p. 109). Common numbers are date of birth, wedding anniversary, and social security number. Interviews with a suspect and knowledge of the suspect can narrow down the possibilities for plausible passwords. Since most humans have a limited ability to remember a large number of passwords, most people reuse the same simple password for several applications (Kruse & Heiser, 2002, p. 110). If the investigator already has discovered a valid password during an earlier phase of the investigation, it is worth trying that password again. Conduct Software AttackIf the suspect was not cooperative, or if efforts to guess the password were unsuccessful, the investigator will need to turn to various software solutions or brute force attack methods. There are several software tools available to recover or remove passwords. A tool suggested by Kruse and Heiser (2002) is Cain. Cain can instantly return a list of cached passwords, password dictionary testing, and brute force checks on Microsoft systems (p. 110). Fisher (2007) recommended four free password recovery tools for Windows: Ophcrack, Cain & Abel, LCP, and John the Ripper (¶ 1). A search on the Internet for password recovery tools will reveal a wealth of information about recovering simple passwords. When suspects use secret and public key encryption schemes they invoke a higher degree of protection that protects data from simple recovery tools. An investigator must expect and be prepared to encounter this type of protection. This higher degree of protection makes it more difficult for forensic investigators to access digital evidence (Casey, 2002, p. 4). Capture KeystrokesSoftware and hardware devices exist that can capture every keystroke a suspect enters on his computer. These programs can reveal passwords and public keys entered by a suspect. The FBI successfully used a keystroke capture program called Magic Lantern to help convict the mobster, Nicodemo Scarfo (Weimann, 2006, p. 188). In July 2007, the US Drug Enforcement Administration used key logging software to convict Mark Forrester and Dennis Alba on charges including “manufacturing and distributing the controlled substance 3,4 Methylenedioxyamphetamine, commonly known as ‘ecstasy’” (Lam, 2007, p2). Using this type of invasive software raises important privacy issues (Weimann, 2006, p. 189), but for now, these tools remain a valuable addition to a digital investigator’s toolkit. Although encryption can be a formidable hurdle in a forensic examination of digital evidence, it is not insurmountable. Providing attorneys and investigators with plaintext fragments of encrypted documents gives them leverage in a case and may even be sufficient to obtain a conviction. Furthermore, with the knowledge and tools described in this paper, a forensic examiner may be able to obtain or guess encryption passphrases, enabling them to decrypt all associated evidence. However, with the growing number and sophistication of encryption and data hiding tools, it is difficult for an individual forensic examiner to keep pace. This difficulty can be reduced by improvements in tools and increased information sharing among examiners. (Casey, 2002, p. 22) The most important take away from this article is that a digital investigator must preserve the original state of data used as evidence. Always make a forensic copy of the original data before investigating the contents of a disk or other storage medium (including volatile computer memory). Both physical and digital crime scene investigations are composed of basic building blocks. The basic phases for both physical and digital investigations are: preserve the scene; survey for evidence; document evidence and scene; search for evidence; reconstruct the scene; and present a theory. Physical and digital evidence are combined to create a complete theory about the crime scene. Searching for evidence frequently is obstructed by encryption, but it is not an insurmountable obstacle. Appropriate methods and tools, employed by a skilled professional digital investigator are the key to recovering encrypted data. It is not easy, but when successful, it is worth the effort. Armstrong, I. (2002, August). Computer forensics: Detecting the imprint. SCMagazine.com, August 2002, 1-10. [Electronic version]. Retrieved November 1, 2007 from http://www.tlsi.net/articles/SCMagazine0802.pdf Brown, C. L. T. (2006). Computer evidence: Collection and preservation. New Delhi: Laxmi. Carney, M. and Rogers, M. (2004, Spring). The Trojan made me do it: A first step in statistical based computer forensics event reconstruction. International Journal of Digital Evidence, 2(4), 1-11. [Electronic version]. Carrier, B. and Spafford, E. H. (2003, Fall). Getting physical with the digital investigation process. International Journal of Digital Evidence, 2(2), 1-20. [Electronic version]. Retrieved October 16, 2007 from http://www.scm.uws.edu.au/compsci/computerforensics/Online%20Materials/ijde_physical.pdf Carrier, B. (2005). File system forensic analysis. Indianapolis: Pearson. Casey, E. (2002, Fall). Practical approaches to recovering encrypted digital evidence. International Journal of Digital Evidence, 1(3), 1-26. [Electronic version]. Fisher, T. (2007). Top 4 free Windows password recovery tools. Retrieved November 6, 2007 from http://pcsupport.about.com/od/toolsofthetrade/tp/passrecovery.htm Jones, K. J, Bejtlich, R., and Rose, C. W. (2006). Real digital forensics: Computer security and incident response. Indianapolis: Pearson. Kruse II, W. G. and Heiser, J. G. (2002). Computer forensics: Incident response essentials. Indianapolis: Pearson. Lam, C. C. (2007). Lengthy sentences for convicted ecstasy laboratory operators. News Release from Office of the United States Attorney Southern District of California. Retrieved November 8, 2007 from http://www.usdoj.gov/usao/cas/press/cas50526-1.pdf Rowlingson, R. (2004, Winter). A ten step process for forensic readiness. International Journal of Digital Evidence, 2(3), 1-28. [Electronic version]. Weimann, G. (2006). Terror on the internet: The new arena, the new challenges. Washington, DC: United States Institute of Peace. Whitcomb, C. M. (2002, Spring). An historical perspective of digital evidence: A forensic scientist’s view. International Journal of Digital Evidence, 1(1), 1-9. [Electronic version]. |
||||
|