 |
Interesting Articles about Popular Topics |
|
|
Dave Carlson - June 21, 2007 (Updated February 18, 2013) Terrorism has changed civilization forever. Terrorism is an elusive concept and difficult to define, but it exists and has significant impact on the world. At the foundations of terrorist organizations are underlying conditions which provide optimal conditions for birth and growth. The economic impact of terrorism has been greater than the entire gross national product of most individual countries. The United States has identified forty-two Foreign Terrorist Organizations, many of them with direct and related ties to al-Qaeda. Effective counter-terrorist strategies must include a method to discover and render ineffective a terrorist organization’s ability to interact. The current anti-terrorist strategy of the United States is to defeat terrorist organizations, deny terrorist support, diminish underlying conditions, and defend the United States. On September 11, 2001, Americans were reminded that the overweening power that they had taken for granted over the past dozen years is not the same as omnipotence. What is less obvious but equally important is that the power is itself part of the cause of terrorist enmity and even a source of U.S. vulnerability. (Betts, 2002, p. 386) Many events have changed civilization forever. Among some of the more influential events that changed various civilizations include: the industrial revolution, discovery of fire, invention of the computer, emergence of religious leaders, evil deeds of war criminals, introduction of sliced bread, rise and fall of the Roman Empire, the ice age, and the life and death of Elvis. An influential event can leave a positive or negative impact on civilization. The most influential negative event in recent U.S. history was the September 11, 2001 terrorist attack on the World Trade Center in New York City, The Pentagon in Washington, D. C., and a remote location in rural Pennsylvania. The devastating events of 9-11 changed numerous aspects of life in the United States and most nations on the planet. Terrorism has changed civilization forever. What is terrorism? Sometimes it depends on who is writing the definition and about whom they are writing. Very few people have a problem with defining the word terror, but many people struggle with the definition of the word terrorism Ahmad (1998) observed that terrorists change over time. “The terrorist of yesterday is the hero of today, and the hero of yesterday becomes the terrorist of today” (p. 47). It is important to understand and accept the changing nature of terrorism before discussing the subject in an academic setting. Additionally, as the faces and methods of terrorism evolve or degrade, we need to be constantly vigilant to protect our nation and chosen way of life. In a 1988 study, Schmid and Jongman (1988) identified 109 definitions of terrorism (p. 5). Of the twenty-two most frequent elements of the definitions, only three occurred in more than half of the diverse definitions: violence, force (83.5%); political (65%); and fear, terror emphasized (51%). Additionally, threat appeared in 47% of the definitions (Schmid & Jongman, 1988, pp. 5-6). Based on those findings, a composite short definition of terrorism could be: Using, or threatening to use, forceful violence to create political change coerced by fear. We have seen their kind before. They are the heirs of all the murderous ideologies of the 20th century. By sacrificing human life to serve their radical visions—by abandoning every value except the will to power—they follow in the path of fascism, and Nazism, and totalitarianism. And they will follow the path all the way, to where it ends: in history’s unmarked grave of discarded lies. (Bush, 2003, p. 5) 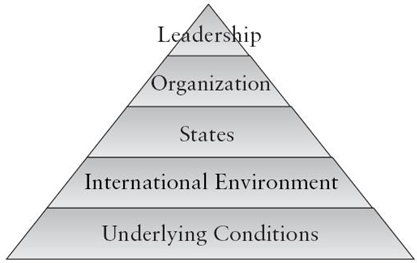 President George W. Bush (2003) laid out "The Nature of the Terrorist Threat Today" in his National Strategy for Combating Terrorism. Figure 1 represents President Bush’s concept of the structure of the terrorism environment (p. 6). Underlying ConditionsBush (2003) identified some of the basic underlying conditions that form the base of the structure that supports and nurtures the growth of terrorism in today’s world. He stated that poverty, corruption, religious conflict, and ethnic strife all create opportunities ripe for terrorist exploitation (p. 6). Specific key events frequently encouraged the formation of terrorist organizations or provided the catalyst to escalate the efforts of an existing terrorist organization (Ranstorp, 1996, p. 157). Ranstorp (1996) observed that many terrorist groups are compelled to pursue a political agenda with the express purpose of securing the release of an imprisoned member or elimination of key opponents (p. 162). Additionally, it is a natural tendency of have-not humans to become jealous of those who have what the have-nots do not possess; as illustrated by terrorist groups using U. S. power as a catalyst for their rage (Betts, 2002, p. 386). Realistic hands-on training and successful outcomes add significant influence to the growth of almost any enterprise. A contemporary condition aiding the expansion of terrorist activity is battlefield experience in Iraq and Afghanistan. Brimly (2006) warnd his readers to be seriously concerned about the consequences of jihadist militants acquiring a high level of combat experience and battlefield expertise in urban warfare, then returning to their home countries to share what they have learned (p. 39). Experienced jihadist fighters represent a pool of leaders and potential members of new terrorist cells in an ever-expanding network (p. 39). Sometimes underlying conditions influence the method terrorist organizations choose to carry out their attacks. Sheikh Fadlallah, Hezbollah’s spiritual leader, explained an underlying condition that motivates many suicide bombers when he said that “there is no difference between dying with a gun in your hand or exploding yourself. In a situation of struggle or holy war you have to find the best means to achieve your goals” (Ranstorp, 1996, p. 159). Dolnik (2003) further asserted that it is absolutely necessary for any terrorist to possess an unwavering belief in the absolute nature of the cause to kill in its name (p. 253). An additional reason why suicide bombings are increasing is offered by the Rand Corporation’s chronology of international terrorism incidents. Statistics reveal that “suicide attacks on average kill four times as many people as other terrorist acts (Hoffman, 2003, p. 338). In light of this revelation, it is not surprising why this method of delivering terror has increased in popularity over the past several years -- it is strategically economical and extremely effective. International EnvironmentFreer, more open borders between countries nurtures the environment that creates access to havens, capabilities, and other support to terrorist organizations (Bush, 2003, p. 6). McCaffrey & Basso (2003) cited this principle to caution about the convergence of terrorist organizations and transnational criminal elements (p. 322). International criminal elements have numerous and varied established routes for passing items and information to all parts of the world. Some terrorist organizations are adopting a long-standing successful business model of seeking out international partners to provide missing organic capability (McCaffrey & Basso, 2003, p. 327). Although, McCaffrey & Basso (2003) pointed out that some observers question the idea of criminal groups having the motivation to associate with known terrorist groups. The assumption by some of these analysts is that collaboration with terrorists would generate increased law enforcement attention, something no criminal organization favors (p. 327). A super-set to the international environment is cyberspace. This blend of real-world and virtual-world environments makes it nearly impossible for U. S. authorities to find and completely eliminate the on-line presence of terrorist groups (Cordesman, 2002, p. 168). These groups have been met by little or no resistance in this cyber-world (Gruen, 2005, p. 352). Gruen (2005) studied the use of the Internet by terrorist organizations and concluded that terrorists have “been able to establish a presence for themselves in nearly every chat room and message board their young target would likely visit” (p. 352). StatesTerrorists obviously need to live and meet in some physical space on the planet, even if only for brief encounters. Several nations are known to provide havens (both willingly and unwittingly) and support (both openly and covertly) for terrorists. Libya and Sudan continued to take significant steps to cooperate in the global war on terror. Cuba, Iran, North Korea, and Syria, however, continued to maintain their ties to terrorist groups. Iran and Syria routinely provide unique safe haven, substantial resources and guidance to terrorist organizations. State sponsors of terrorism provide critical support to non-state terrorist groups. Without state sponsors, terrorist groups would have much more difficulty obtaining the funds, weapons, materials, and secure areas they require to plan and conduct operations. Most worrisome is that some of these countries also have the capability to manufacture WMD and other destabilizing technologies that can get into the hands of terrorists. The United States will continue to insist that these countries end the support they give to terrorist groups. (U.S. Department of State, 2006, ¶ 1) A national state does not need to consciously support terrorist groups to be an asset to the formation of a codling environment for terrorists. Sometimes efforts of nations to reduce terrorist activity actually flame the fires of opposition. A prime example of this is the current condition in Iraq. Former CIA Director Porter Gross observed that Iraq has become a magnet for Jihadists (Downing, 2005, p. 438). Organization“Once entrenched in a safe operating environment, the organization can begin to solidify and expand” (Bush, 2003, p. 6). Depending on the environment, the organization can determine an appropriate structure to support planned operations, find and secure needed resources, expand membership, establish adequate security and communication channels, put in place logistics support, and dominate its area of influence. Today’s terrorist organizations are flexible and rely more on networked structures than traditional hierarchical configurations. Terrorist groups draw strength and support from sympathetic groups in different areas, frequently crossing international borders to conduct combined terror campaigns. This networked collaborative structure allows groups, such as al-Qaida, to function effectively in transnational and global theaters of operation (Bush, 2003, p. 8). Because of effective networked organizations, Betts (2002) noted that “only small numbers of competent terrorists need survive and operate to keep the threat to American society uncomfortably high” (p. 393). A strength of current terrorist organizations is that it is difficult for anyone from the outside to penetrate a network of independent cells. Sleeper cells remain hidden in plain sight and generally are unknown to other organizations. Additionally, the ultimate success of a terrorist network is directly proportional to the effectiveness of its leadership. LeadershipAt the structure’s pinnacle, “terrorist leadership provides the overall direction and strategy that links all these factors and thereby breathes life into a terror campaign” (Bush, 2003, p. 6). Terrorist leadership can take the form of a single charismatic individual, a close-knit group of like-minded individuals, or an over-arching common philosophy. The most powerful leadership force in a terrorist movement is an over-arching common philosophy. There is no individual or core cadre to identify and target for removal. Coll & Glasser (2005) refer to many terrorist activities as part of the “al-Qaeda movement” (¶ 2). They espouse that al-Qaeda is “more a brand than a tight-knit group” (¶ 3) and “has evolved from headquarter-planned conspiracies toward diffuse ideological incitement” (¶ 10). Abu Jandal, a former member of Bin Laden’s personal staff, was quoted in the newspaper Al-Quds Al-Arabi as saying: “Every element of al Qaeda is self-activated. Whoever finds a chance to attack just goes ahead. The decision is theirs. This is regardless of whether they pledged allegiance to Sheik Osama bin Laden or not” (Coll & Glasser, 2005, ¶ 11). Terrorism has had a significant negative financial impact on the world. Because of the limited scope of this paper, further discussion will focus primarily on the economic impact of the 9/11 attack and related events on the United States. The most significant terrorist act within the borders of the United States occurred on September 11, 2001 with the destruction of both buildings of the World Trade Center and a portion of the Pentagon. The devastation killed more than 3,000 people, negatively impacted 300 businesses, eliminated or relocated almost 200,000 jobs, destroyed four large commercial aircraft, and caused direct property losses of $20-30 billion (Gheno & Lee, 2006, p. 210). Additionally, the impact on financial markets was swift and pronounced. “Stock prices tumbled, spreads between corporate and government bond yields, as well as spreads between emerging market and U.S. bond index yields widened” (Gheno & Lee, 2006, p. 211). Fortunately, Gheno & Lee (2006) discovered that the negative impact on the market was “financial and transitory, rather than fundamental and persistent” (p. 215). Considering the $20-30 billion impact on the United States economy and the resulting mega-billions spent to date on the General War on Terror (GWOT), the 9/11 attack generated an enormous return on investment for the estimated $200,000 it cost al-Qaeda to culminate years of planning in a successful attack (Langelett & Schug, 2004, p. 161). The 9/11 attacks and subsequent consequences may have done immeasurably more damage than al-Qaeda ever imagined possible. Langelett & Schug (2004) maintain that the events forced a weakening economy further into recession, psychological effects adversely affected consumer spending, air travel decreased at the same time oil prices increased, insurance companies were faced with large payments that forced rate increases, and manufacturers worried about disruption of supplies reconsidered just-in-time inventory management practices (p. 164). Unfortunately, there also is a good economic side to increased terrorism. Stocks related to Homeland Security have more than tripled since the 9/11 attacks (Palmer, 2005, p. 22). In addition to traditional defense products, physical screening, biometric identification, network security, tracking systems, and surveillance systems all have seen dramatic increases in sales, both at home and abroad (Palmer, 2005, p. 23). Every two years (odd-numbered years) the United States Secretary of State publishes a list of foreign organizations designated as Foreign Terrorist Organizations (FTOs). “FTO designations play a critical role in our fight against terrorism and are an effective means of curtailing support for terrorist activities and pressuring groups to get out of the terrorism business” (Office of Counterterrorism, 2005, ¶ 1). There are three legal criteria (authorized by Section 219 of the Immigration and Nationality Act (INA), as amended) to determine if an organization can be designated as a FTO:
Terrorist organizations frequently have multiple purposes. Generally, FTOs can be categorized as primarily religious or non-religious organizations. Many times there is a fuzzy line between the two distinctions. At their root, all terrorist organizations have a political agenda. Of the 42 designated Foreign Terrorist Organizations, 24 are primarily religious and 18 are mainly non-religious in their focus. Non-religious organizations do not have a monopoly on coercing political action. Organizations motivated by religion have a strong political agenda. Most obvious is the impossibility of separating religion and politics by Muslim groups, as Islam makes no distinction between religion and politics (Dolnik, 2003, p. 245). Many religious terrorist organizations believe they “have an absolute monopoly of the revealed truth by God (Ranstorp, 1996, p. 156). “The greatest threat and the most wanted terrorists come from the al-Qaida (AQ) network, which includes a core al-Qaida organization and numerous confederated extremist groups” (U.S. Department of State, 2007, ¶ 1). Many terrorists modify their organizational structure into loosely-networked groups to accomplish various missions together against a common enemy -- the United States and its allies (Arquilla, Ronfeldt, & Zanini, 1999, p. 111). The only truly effective counterterrorism efforts sever the connections between terrorist’s strategic desires and their operational or tactical efforts (Brimley, 2006, p. 31). Brimley (2006) asserts that “understanding, targeting, and eliminating transnational support networks should be a main effort of counterterrorism strategy” (p. 33). He further suggests that many counterterrorism efforts fail because they concentrate on specific features, such as ideology, strategy, tactics, or finance, instead of framing their efforts around a holistic picture of the organization’s overall composition; specifically, how each feature and capability fits into the larger whole (p. 34). A significant role in countering the spread of terrorism is to learn about and adapt to methods these nefarious organizations use to interact. A specific example is the use of the Internet to communicate, disseminate propaganda, conduct marketing campaigns, and raise funds to support their efforts (Weimann, 2006, p. 51). Weimann (2006) observed that the majority of policymakers, journalists, and scholars concentrate the “overrated threat posed by cyberterrorism or cyberwarfare (i.g., attacks on computer networks, including those on the Internet)” instead of focusing on the real threat: daily use of the Internet (p. 51). Pillar (2004) predicted that the greatest future challenge for countering terrorism in the United States is to sustain the population’s determination to fight and win. He observed that history has shown the U.S. public tends to rally around a cause when there is a significant event, such as the 9/11 attacks, then gradually looses interest as time passes without any grandiose reappearance of terrorist activity that directly impacts their lives (p. 479). “The further events of September 11 fade into the past, the more difficult it will be to keep Americans focused on the danger posed by terrorism” (Pillar, 2004, p. 480). Al-Qaeda clearly has more ambitious objectives than most terrorist organizations; it seeks to expel the most powerful state in history from a part of the world that has been central to U.S. foreign policy for more than half a century, and it intends to do so without a large standing military. (Posen, 2001, p. 463) Military strategies of the past are ineffective against modern terrorist operations. The United States and the rest of the world affected by terrorism must develop and employ new strategies to ensure any possibility of controlling terrorism. America and its partners must follow a similar path as Israel’s transformation to deal with terrorist activity. Israel learned that large armed forces trained, structured, and equipped for conventional war are incapable of effectively dealing with insurgents (de Wijk, 2001, p. 512). While there is no guarantee of success, Israel discovered that small task forces, new tactics, special weapons systems, and smaller scale operations are a step in the right direction (de Wijk, 2001, p. 512). An effective strategy for combating terrorism is to cut off the terrorist’s source of funding. One source of funding is from numerous Islamic charities. The flow of cash from Islamic charities is rarely regulated, and when it is, the controls are very loose. The down side to shutting down the flow of Islamic charities is the problems it may cause for the numerous good causes they support (Basile, 2004, p. 420). An occasional unplanned bright spot emerges in the fight against terrorism. Sometimes unpredicted circumstances intervene or technology hurdles are too great to overcome. Recent history revealed technological problems encountered by a Japanese terrorist organization in their failed attempts to inflict casualties on their target population through the use of biological weapons of mass destruction. Even Aum Shinkikyo, the infamous Japanese cult which possessed an estimated $1 billion in assets, some 20 university-trained microbiologists working in top-notch research facilities, and the freedom to conduct unlimited experiments, completely failed in all 10 attempts to attack with anthrax and botulinum toxin. (Dolnik, 2003, p. 258) In 2003, President George W. Bush shared his strategic intent for combating terrorism. “The intent of our national strategy is to stop terrorist attacks against the United States, its citizens, its interests, and our friends and allies around the world and ultimately, to create an international environment inhospitable to terrorists and all those who support them.” (Bush, 2003, p. 11) He explained that the United States would simultaneously act on four fronts: 1) Defeat Terrorist Organizations De Wijk (2001) urges diplomacy over military action. He advocates targeted campaigns to win the hearts and minds of the people. He cautions against unconstrained military force because “using military means may exacerbate the potential that this campaign will be cast as a clash of civilizations, ultimately making the problem of terrorism even worse” (p. 517). It may not be possible to defeat all terrorists and eliminate all forms of terrorism in our lifetimes, but we must be vigilant and never give up the struggle. “The best we may be able to achieve is to understand that we live in danger, without living in fear” (Howard, 2005, p. 101). Build on each small victory and do not let the terrorist enemy regain a foothold in any of the hard-won real estate or ideological mindset. Terrorism is an elusive concept -- difficult to define -- but it does exist and has significant impact on the world. At the foundations of terrorist organizations are underlying conditions which provide optimal conditions for birth and growth. The economic impact of terrorism has been greater than the entire gross national product of most individual countries. The United States has identified forty-two Foreign Terrorist Organizations, many of them with direct and related ties to al Qaeda. Effective counter-terrorist strategies must include a method to discover and render ineffective a terrorist organization’s ability to interact. The current anti-terrorist strategy of the United States is to defeat terrorist organizations, deny terrorist support, diminish underlying conditions, and defend the United States. Ahmad, E. (1998). Terrorism: Theirs & ours. In Howard, R. D. and Sawyer, R. L. (2005). Terrorism and counterterrorism: Understanding the new security environment, readings and interpretations (2 ed.) (pp. 46-52). New York: McGraw-Hill. Arquilla, J., Ronfeldt, D., and Zanini, M. (1999). Networks, netwar, and information-age terrorism. In Howard, R. D. and Sawyer, R. L. (2005). Terrorism and counterterrorism: Understanding the new security environment, readings and interpretations (2 ed.) (pp. 107-129). New York: McGraw-Hill. Basile, M. (2004). Going to the source: Why Al Qaeda’s financial network is likely to withstand the current war on terrorist financing. In Howard, R. D. and Sawyer, R. L. (2005). Terrorism and counterterrorism: Understanding the new security environment, readings and interpretations (2 ed.) (pp. 416-432). New York: McGraw-Hill. Betts, R. K. (2002). The soft underbelly of American primacy: Tactical advantages of terror. In Howard, R. D. and Sawyer, R. L. (2005). Terrorism and counterterrorism: Understanding the new security environment, readings and interpretations (2 ed.) (pp. 386-401). New York: McGraw-Hill. Brimley, S. (2006, Summer). Tentacles of Jihad: Targeting transnational support networks. Parameters, 36(2), 30-47. Bush, G. W. (2003). National strategy for combating terrorism. [Electronic version]. Washington: Government Printing Office. Retrieved June 12, 2007 from http://www.state.gov/documents/organization/60172.pdf Coll, S. and Glasser, S. B. (2005). Attacks bear earmarks of evolving Al Qaeda. Retrieved June 13, 2007 from http://www.washingtonpost.com/wp-dyn/content/article/2005/07/07/AR2005070702389_pf.html Cordesman, A. H. (2002). Cyber-threats, information warfare, and critical infrastructure protection: Defending the U.S. homeland. Westport, CT: Greenwood Publishing Group. de Wijk, R. (2001). The limits of military power. In Howard, R. D. and Sawyer, R. L. (2005). Terrorism and counterterrorism: Understanding the new security environment, readings and interpretations (2 ed.) (pp. 505-517). New York: McGraw-Hill. Dolnik, A. (2003). All God’s poisons: Re-evaluating the threat of religious terrorism with respect to non-conventional weapons. In Howard, R. D. and Sawyer, R. L. (2005). Terrorism and counterterrorism: Understanding the new security environment, readings and interpretations (2 ed.) (pp. 242-262). New York: McGraw-Hill. Downing, W. A. (2005). The global war on terrorism: Re-focusing the national strategy. In Howard, R. D. and Sawyer, R. L. (2005). Terrorism and counterterrorism: Understanding the new security environment, readings and interpretations (2 ed.) (pp. 435-453). New York: McGraw-Hill. Gheno, A. and Lee, S. L. (2006). The impact of 9/11 on US REIT returns: Fundamental or financial? International Journal of Strategic Property Management, 10, 209-216. Gruen, M. (2005). Terrorist indoctrination and radicalization on the Internet. In Howard, R. D. and Sawyer, R. L. (2005). Terrorism and counterterrorism: Understanding the new security environment, readings and interpretations (2 ed.) (pp. 352-366). New York: McGraw-Hill. Hoffman, B. (2003). The logic of suicide terrorism. In Howard, R. D. and Sawyer, R. L. (2005). Terrorism and counterterrorism: Understanding the new security environment, readings and interpretations (2 ed.) (pp. 337-347). New York: McGraw-Hill. Howard, R. D. (2005). Understanding Al Qaeda’s application of the new terrorism -- The key to victory in the current campaign. In Howard, R. D. and Sawyer, R. L. (2005). Terrorism and counterterrorism: Understanding the new security environment, readings and interpretations (2 ed.) (pp. 91-106). New York: McGraw-Hill. Langelett, G. L. and Schug, M. C. (2004, Jul/Aug). An economic analysis of September 11th. The Social Studies, 95(4), 161-165. McCaffrey, B. R., and Basso, J. A. (2003). Narcotics, terrorism, and international crime: The convergence phenomenon. In Howard, R. D. and Sawyer, R. L. (2005). Terrorism and counterterrorism: Understanding the new security environment, readings and interpretations (2 ed.) (pp. 322-336). New York: McGraw-Hill. Office of Counterterrorism. (2005). Foreign Terrorist Organizations (FTOs). Retrieved June 14, 2007 from http://www.state.gov/s/ct/rls/fs/37191.htm Palmer, J. (2005, July 4). The profits of patriotism: Guarding America. Barron’s, 85(27), 21-23. Pillar, P. R. (2004). Counterterrorism after Al Qaeda. In Howard, R. D. and Sawyer, R. L. (2005). Terrorism and counterterrorism: Understanding the new security environment, readings and interpretations (2 ed.) (pp. 474-483). New York: McGraw-Hill. Posen, B. R. (2001). The struggle against terrorism: Grand strategy, strategy, and tactics. In Howard, R. D. and Sawyer, R. L. (2005). Terrorism and counterterrorism: Understanding the new security environment, readings and interpretations (2 ed.) (pp. 461-473). New York: McGraw-Hill. Ranstorp, M. (1996). Terroism in the name of religion. In Howard, R. D. and Sawyer, R. L. (2005). Terrorism and counterterrorism: Understanding the new security environment, readings and interpretations (2 ed.) (pp. 153-167). New York: McGraw-Hill. Scanlan, G. (2004, December). The war on terror -- Future trends. Journal of Financial Crime, 12(2), 104-112. Schmid, A. P., Jongman, A. J., et al. (1988) Political terrorism: A new guide to actors, authors, concepts, databases, theories, and literature. New Brunswick: Transaction Books. U.S. Department of State. (2006). Country reports on terrorism. Retrieved June 12, 2007 from http://www.state.gov/s/ct/rls/crt/2005/64337.htm U.S. Department of State. (2007). The terrorist enemy. Retrieved June 12, 2007 from http://www.state.gov/s/ct/enemy/ Weimann, G. (2006). Terror on the Internet: The new arena, the new challenges. Washington, D.C.: United States Institute of Peace. |
||||
|